serpretetsky
2[H]4U
- Joined
- Dec 24, 2008
- Messages
- 2,180
Zen2 based CPUs have a new bug discovered which seems pretty bad. Zenbleed.
https://arstechnica.com/information...ug-in-many-amd-cpus-could-take-months-to-fix/
Ouch. list of cpus affected taken from ARStechnica
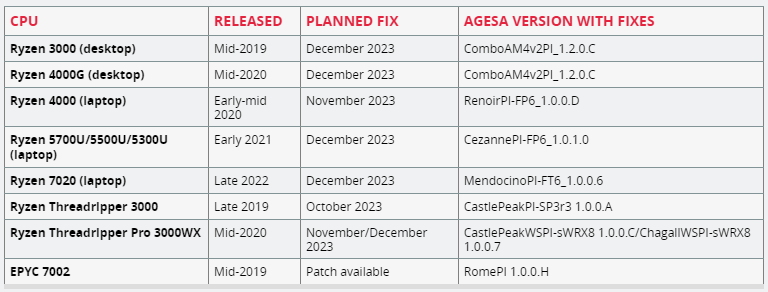
https://arstechnica.com/information...ug-in-many-amd-cpus-could-take-months-to-fix/
The bad news is that the exploit doesn't require physical hardware access and can be triggered by loading JavaScript on a malicious website.
Ouch. list of cpus affected taken from ARStechnica

Last edited:
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)