Armenius
Extremely [H]
- Joined
- Jan 28, 2014
- Messages
- 42,482
In a bid to enhance security for normal users, Bitlocker encryption will now be enabled by default when you install the 24H2 update for Windows 11. You will need to enable a registry entry to prevent encryption if you do not want it on your install. Bitlocker encryption noticeably decreases drive performance, especially on solid state drives, so it is undesirable if you use your machine for any kind of intensive read/write operations. Note that when the update is installed on top of your current installation that it will not take effect immediately; it will only encrypt attached drives upon the update being reinstalled.
https://www.tomshardware.com/softwa...happens-on-both-clean-installs-and-reinstalls
https://www.tomshardware.com/softwa...happens-on-both-clean-installs-and-reinstalls
Regardless, any Windows 11 version that has BitLocker functionality will now automatically have that activated/reactivated during reinstallations starting with 24H2. This behavior applies to clean installs of Windows 11 24H2 and system upgrades to version 24H2. Systems that upgrade to Windows 11 24H2 automatically have the Device Encryption flag turned on, but it only takes effect (for some reason) once Windows 11 24H2 is reinstalled on the machine. Not only is the C: drive encrypted, but all other drives connected to the machine will be encrypted as well during reinstallation.
...
On top of this, BitLocker has been proven to impact system performance, particularly SSD performance. We tested BitLocker encryption last year and discovered SSD performance can drop by up to 45% depending on the workload. Even worse, if you are using the software form of BitLocker, all the encryption and decryption tasks get loaded onto the CPU, which can potentially reduce system performance as well. (Modern CPUs do have hardware-accelerated AES encryption/decryption, but there's still a performance penalty attached.)
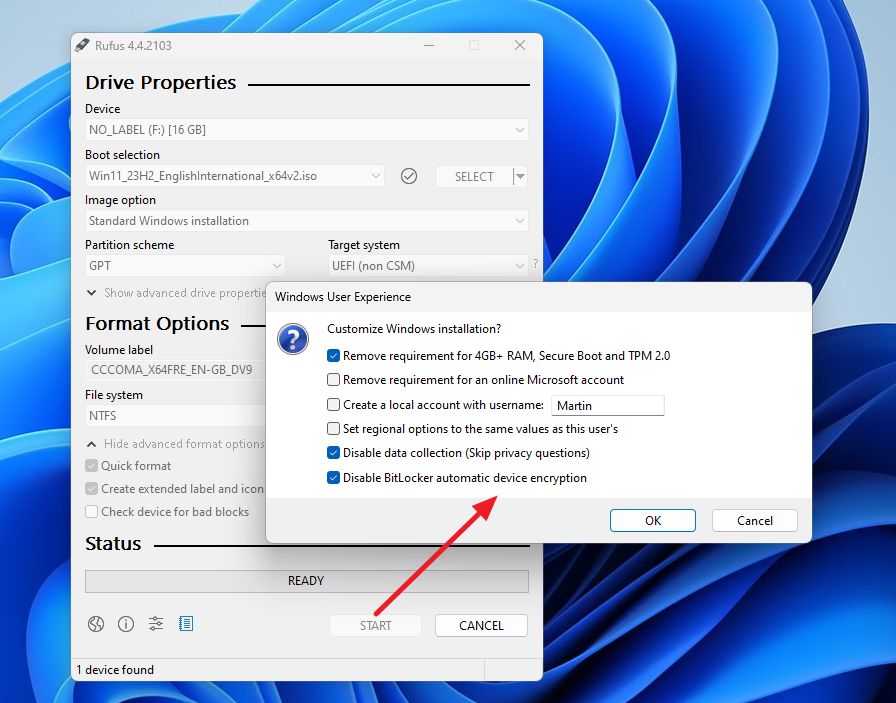
The good news is that disabling BitLocker encryption during a reinstallation isn't difficult. The easiest method is to create a bootable ISO through Rufus USB, which has the ability to disable Windows 11 24H2's drive encryption. Another method is to disable automatic encryption right from the installation wizard, which can be done by opening the Registry through the command prompt (Shift + F10) and changing the BitLocker "PreventDeviceEncryption" key to 1.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)